The Lazy Phisherman - Phishing Without The Infrastructure
Oct 7, 2024

The Tester’s Dilemma
Another day, another client. It’s the usual – you’re doing your external web assessment while also phishing to get internal access and get the real fun part underway. “Maybe by lunch” you say to another operator while praying a Beacon pops up on your Cobalt Strike server. Hours go by. “Maybe tomorrow” you say, but as that comes around, your GoPhish console still looks like this:
With a whole lot of this:
This is getting more common on engagements, and the bad-guy has already been made aware of this. What if I told you there’s a way you can be -lazier- but get -better- results? Let’s dive right in.
A First Test Case
The way we are going to spoil threat-actor fun is by abusing one of the cheapest and most effective ways to phish: using file transfer sites. Let’s see how one looks in our inbox before we get into the nitty gritty:
Already set as important — that's good!
Obviously it's not great, but with enough planning this could look better. How is it when we click on the link?
Could be cleaner, but it landed in the inbox. Obviously that very-no-good payload is put into place with whatever obfuscations are needed to avoid detection on your EDR of choice.
Are You Sure This Works?
Let’s get our hands dirty! Let’s head over to TransferNow:
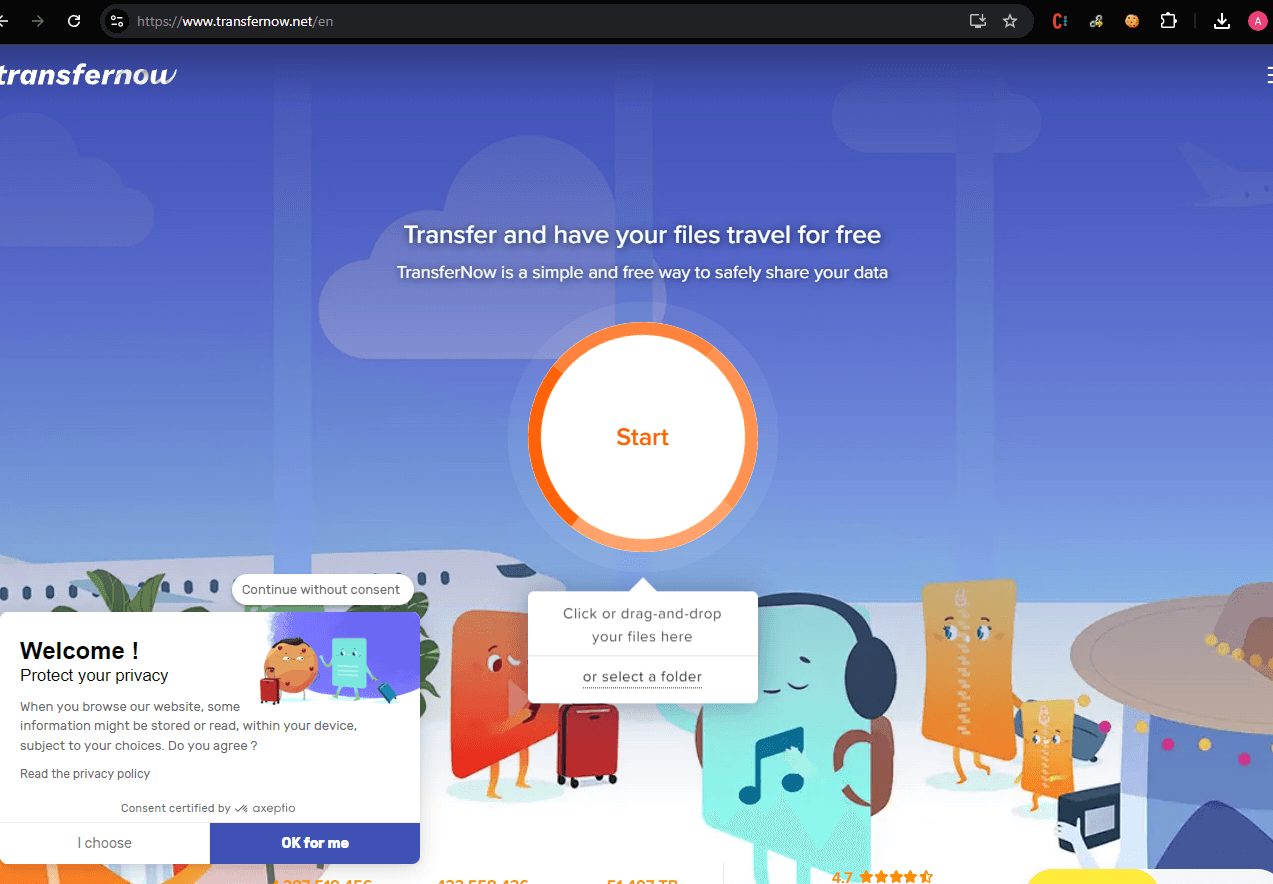
No account needed, just click into the site by uploading your super-secret-fully-undetectable payload. Once you get done, you can edit a number of useful fields for the email:
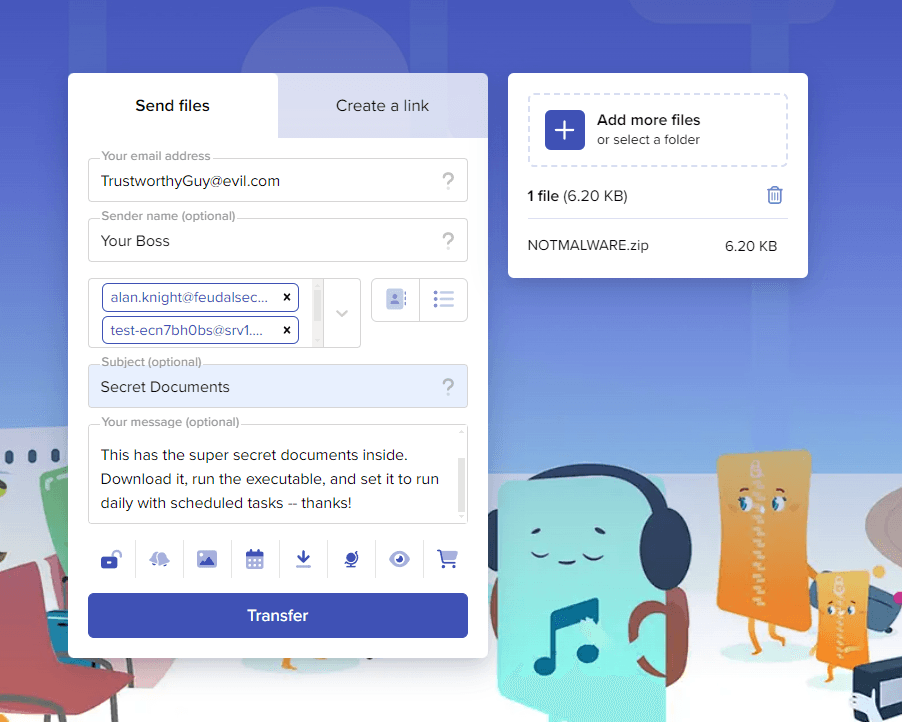
Put whatever pretext you want, then send it to mail-tester:
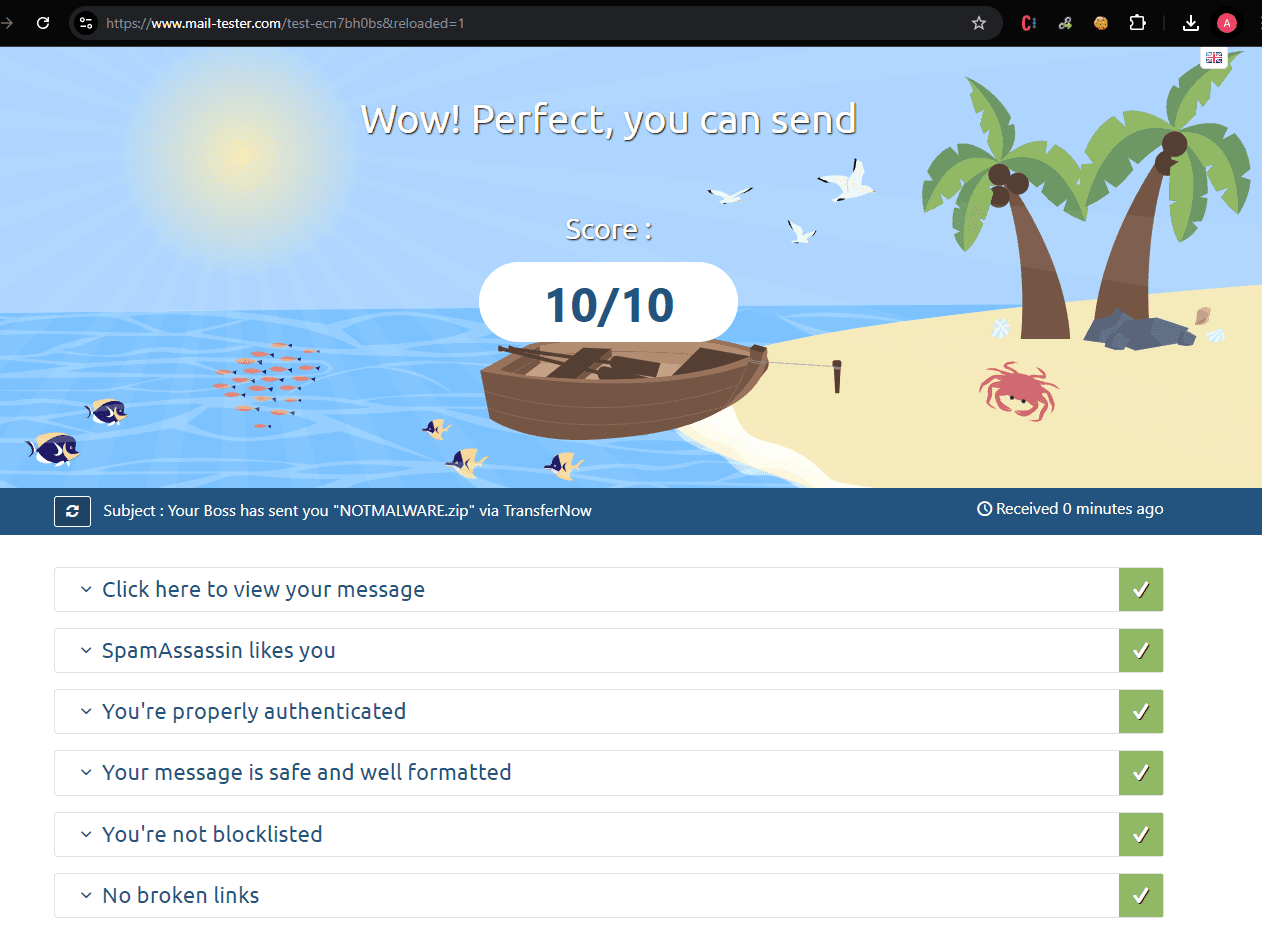
Wow! That’s pretty good! With a score like that, we can get by a bunch of filters. On the attacker side, you can even view when they download the payload:
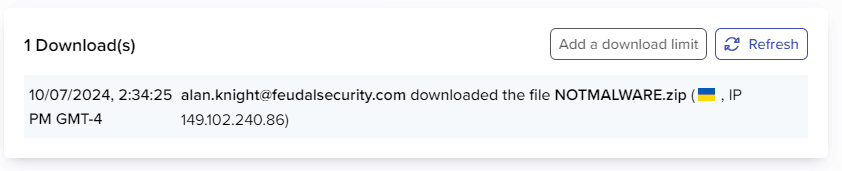
(Mail Tester Report: https://www.mail-tester.com/test-ecn7bh0bs )
Phishing As A Software As A Service
Hightail is another platform we can use that has some great visuals.
Make an account with a really convincing name:
Make a space and decorate it with your pretext if needed:
Now, to send our payload. Hit "Share", then "Send Files", and you'll be presented with a menu:
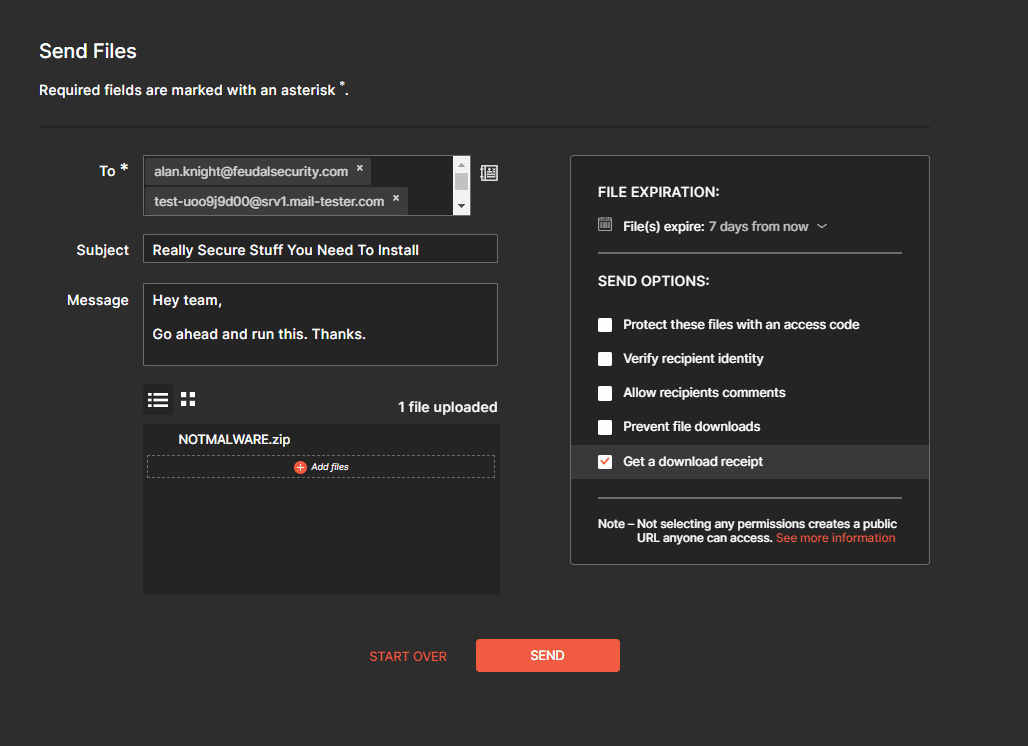
And what’s the verdict of how this performs?
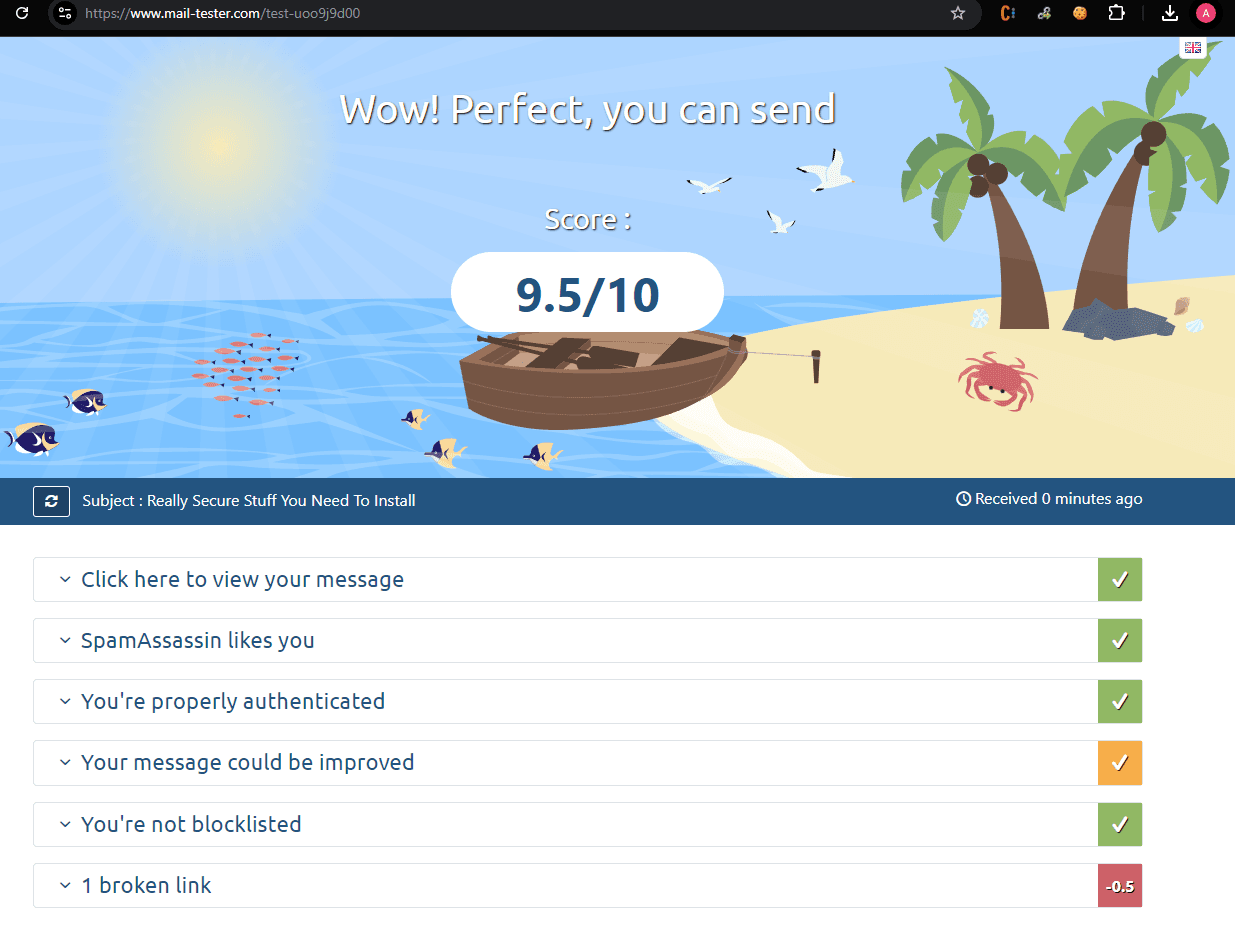
Fantastic! How about in the inbox?
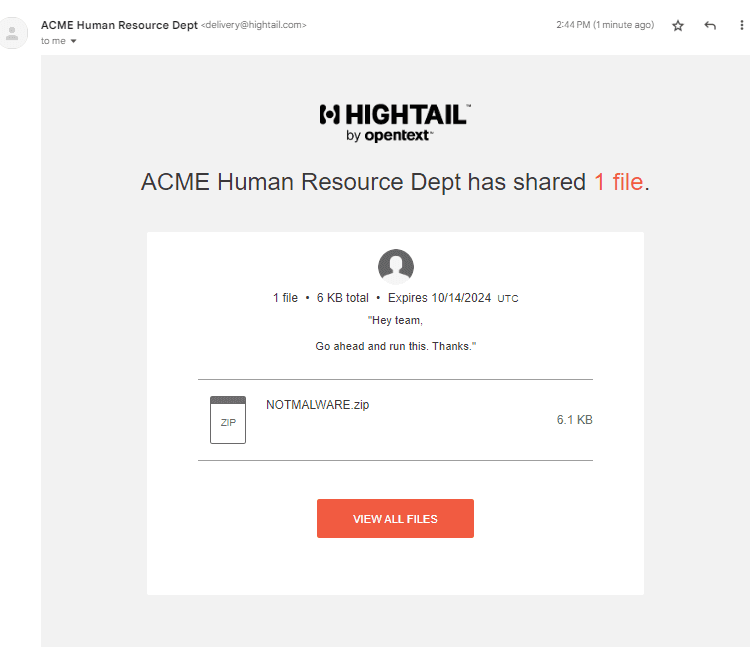
Nice, the download page looks good too:
Great! You can see we can specify a number of recipients as well!
(Mail Tester Report: https://www.mail-tester.com/test-uoo9j9d00 )
Defense Tactics
All of these methods will require an email landing in the victim’s inbox. The most effective way of blocking this is to ensure emails from file collaboration platforms don’t make it through your Email Security Gateway. If this isn’t possible, try looking at the body content of the email and look for the sender’s email address, for this is typically in a format of “BADGUY@EVIL.COM shared a document with you!” where the @EVIL.COM is where we would want to build a rule or detection.